Free Cisco Written Dumps
For Top 50 Purchases 01:59:56
X
ccie virtual lab
Here is the most accurate CISCO CCIE WRITTEN exam questions and answers. All study materials need to be carefully selected by professional certification experts to ensure that you spend the least amount of money, time, and pass the high quality exam. There is also a professional service team that can customize your study plan for you to answer all your questions, PASSHOT's CCIE Written Dumps is definitely the biggest boost for you to test CCIE that helping you pass any Cisco exam at one time.
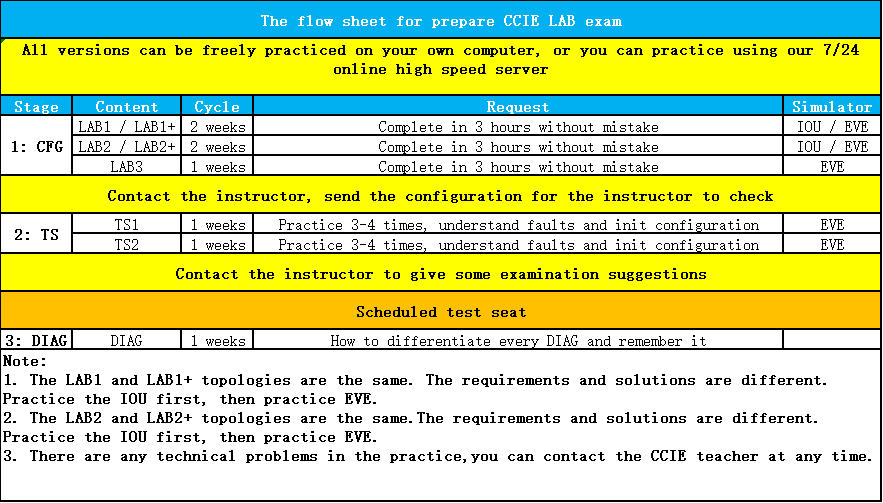
CCIE Routing and Switching LAB Dumps
Exam Code: CFG: LAB1、LAB1+、LAB2、LAB2+、LAB3
TS: TS1(5 sets)、TS2(3 sets)
DIAG:DIAG 1~DIAG 8(8 sets)
Certification Provider: Cisco
Certification Exam Name:CCIE Routing and Switching Lab
Update Date: Feb 21,2026
Numbers of Question & Answers
- 1209 Reviews
ccie virtual lab
No shut
Access-list 100 permit IP any any
technical route honestly. After all, there is still a hobby. At
Serial1 is down, Line protocol is down
Router rip
=========================================================== ===============
IGRP configuration
Second, the problem
FRAME-REL A Y topology (pvc)
2. with set ACL reject absolutely london to Ping through Denver (1)
——————————————
perseverance of learning. Teachers
Interface s 1
Vlan 20
Configuration with multipoint subinterface
Fix: Rebuild after reconfiguration
2. Binary transfer mode
7. When to disconnect
3.TransParent mode of formula < clear >
Suppose you want to deny A to access C now, and assuming you are asking for an ACL on B (of course C can also be), we replace this topology with an example:
Troubleshooting Security Contexts
Managing the Cisco ASA Adaptive Security Appliance Using the CLI
basically two hours. After two hours, the disconnection must be
postal version and gave myself two months. I stayed at home and watched it day and night. Closed
knocking, and I have finished it all over, but I have forgotten it when I
vtp password
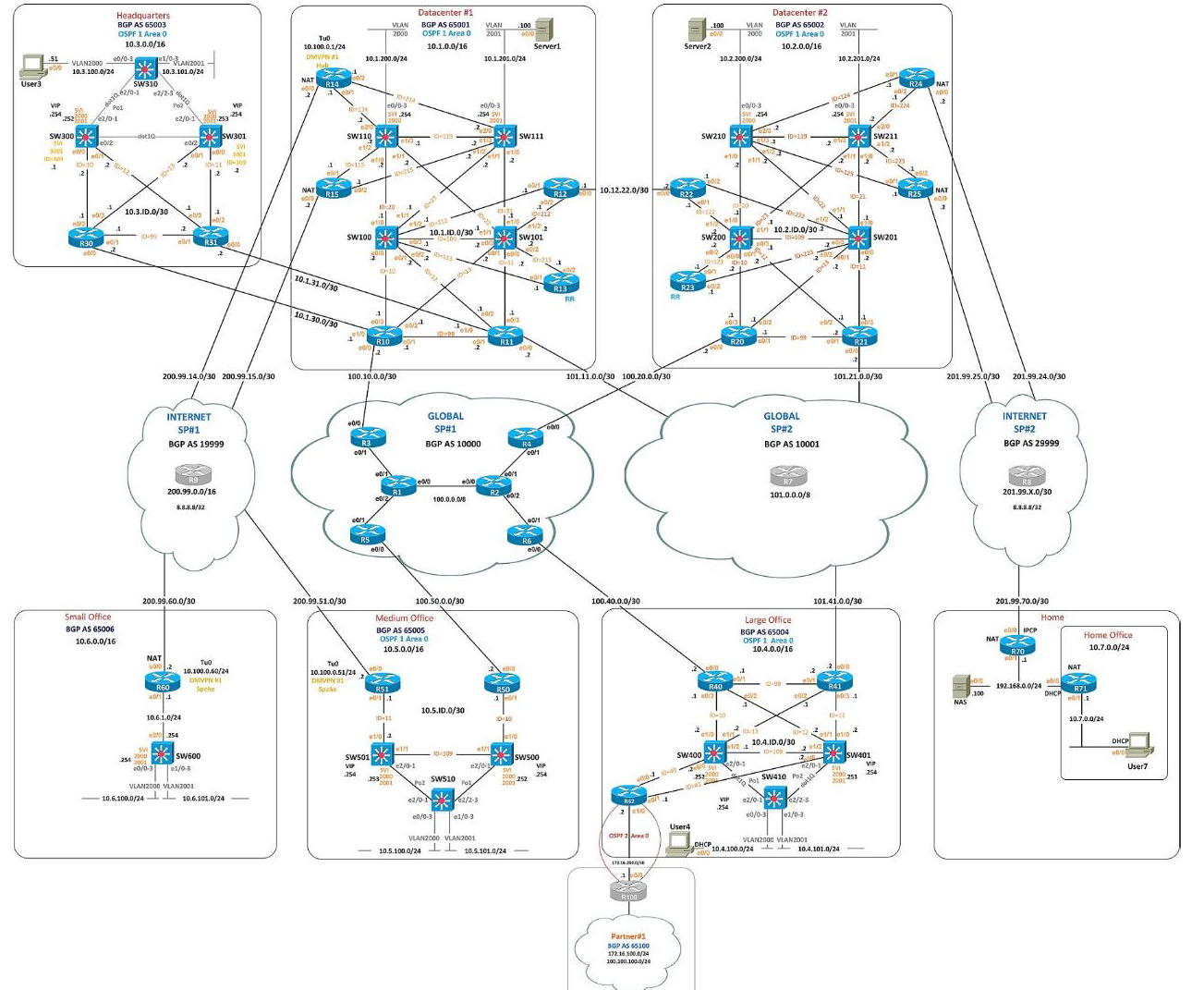
SECTION 1 LAYER 2 TECHNOLOGIES
Section 1.1: LAN Access
The following requirements were pre-configured
l VTP is turned off in all switches
l All required VLAN, including access-ports configuration in all relevant switches are provisioned.
l All required SVI interface in all relevant switches (including IP address and subnets mask) are provisioned.
Configure the network in all sites as per the following requirements:
l Access-port must immediately transition to the forwarding state upon link up, as long as they do not receive a BPDU. Use the minimal number of commands per switch to enable this feature.
l If an access-port receive a BPDU, it must automatically shutdown. Use the minimal commands per switch to enable this feature.
l Ports that were shutdown must attempt to automatically recover after 10 minutes.
l None of the switches may generate a TC.
section 1.2: LAN distribution
configure the headquarters’ network as well as the large and medium office networks as per the following requirements:
l all trunks must use dot1q encapsulation
l negotiation of trunking protocol must be disabled in all switches
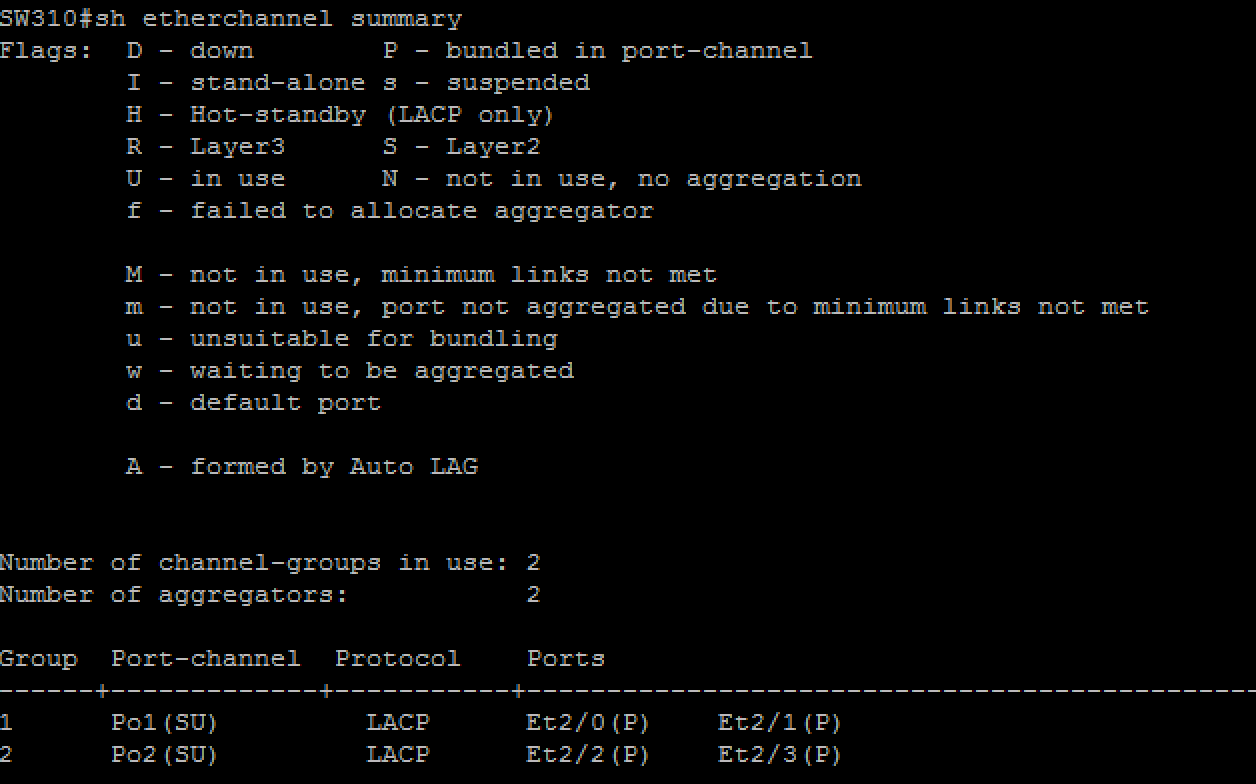
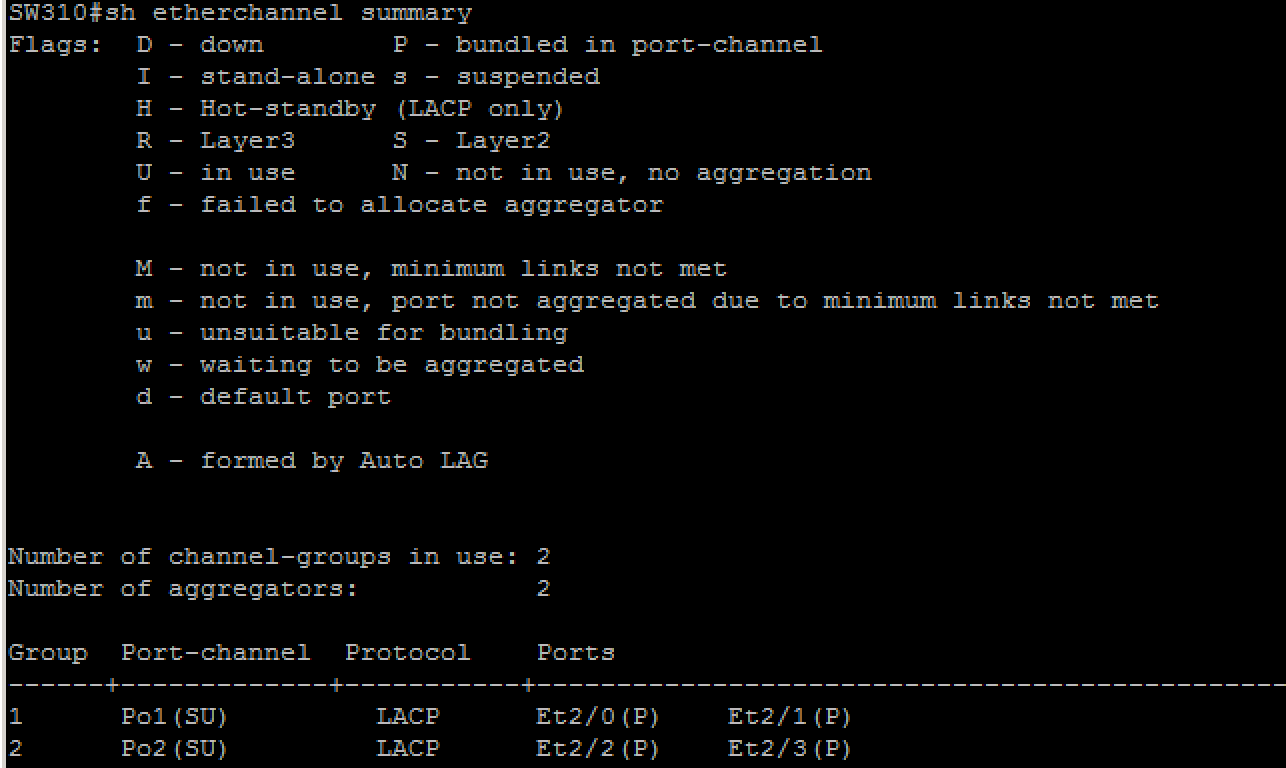
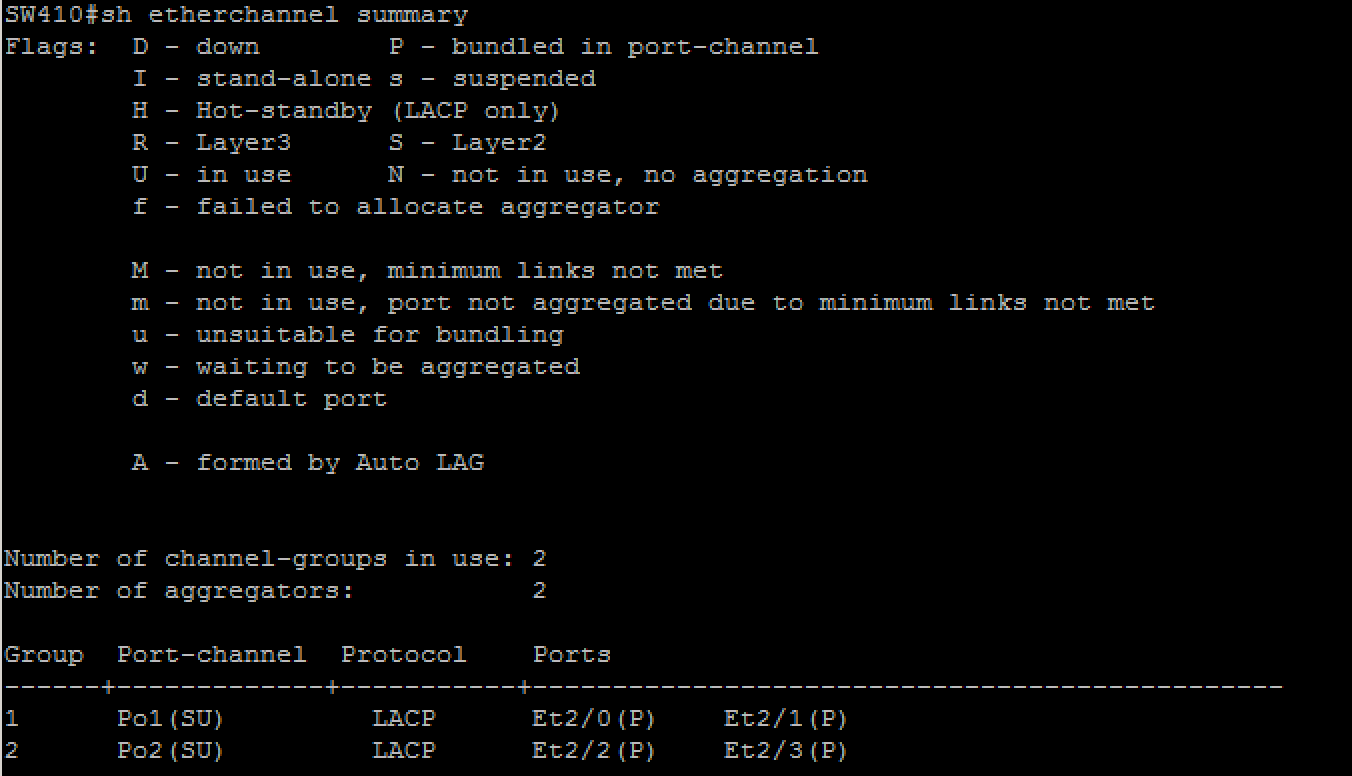
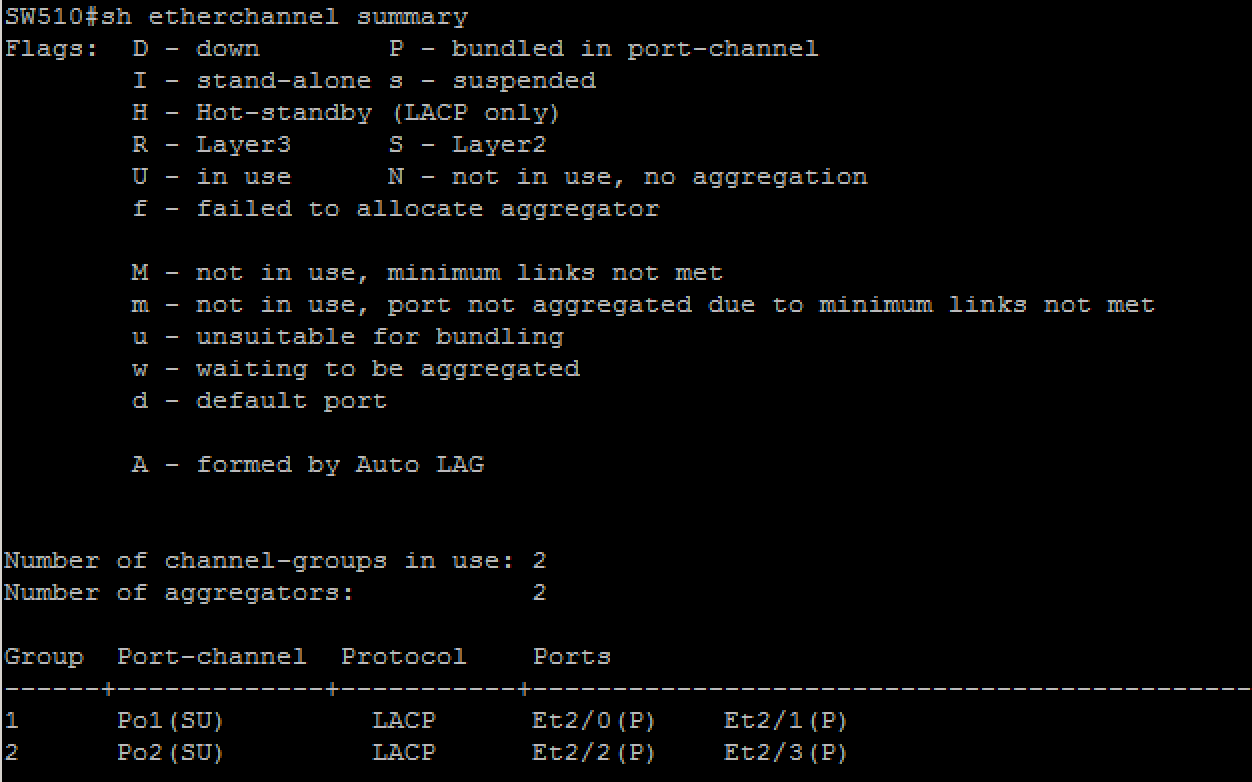
l distribution switches (SW300, SW301, SW400, SW401, SW500, SW501) must initiate etherchannel negotiation using LACP
l configure layer 2 etherechannel’s number as shown in the ‘diagram 1: main topology’ and ‘diagram 5: layer 2 connections’ (that is use only Po1 and/or Po2)
l ensure that all ports included in etherchannels are effectively in use and bundled in the expected channel
l access switches must see similar output as shown below:
section 1.3: LAN resiliency: spanning-tree
configure the headquarters‘network as per the following requirements:
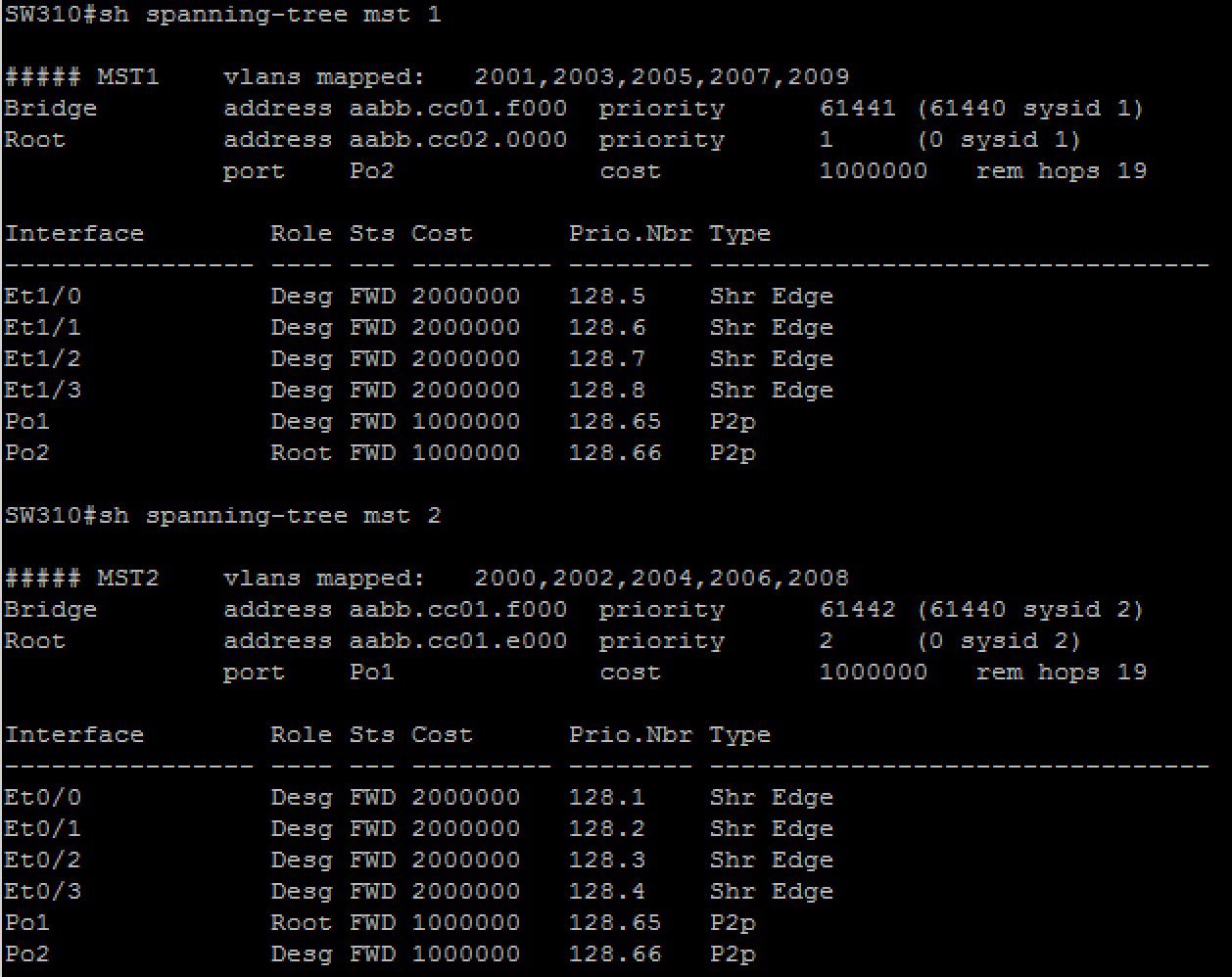
l SW300 must be the spanning-tree root bridge and must maintain a single spanning-tree instance for the following VLANs: 2000, 2002, 2004, 2006, 2008 (use instance number 2)
SW301 must be the spanning-tree root bridge and must maintain a single spanning-tree instance for the following VLANs: 2001, 2003, 2005, 2007, 2009 (use instance number 1)
l all other VLANs, except 3001, must share the default spanning-tree instance
l ensure that interface E0/2 of SW 300 and SW 301 is a dot1q trunk and that it switches frames for VLAN 3001 only
l SW300, SW301, and SW 310 must not have any blocked ports for any access VLAN (2000-2009)
l SW310 must have the least chance of being elected the root bridge for any VLAN
l none of the three switches may run more than four instance of spanning-tree at any point in time
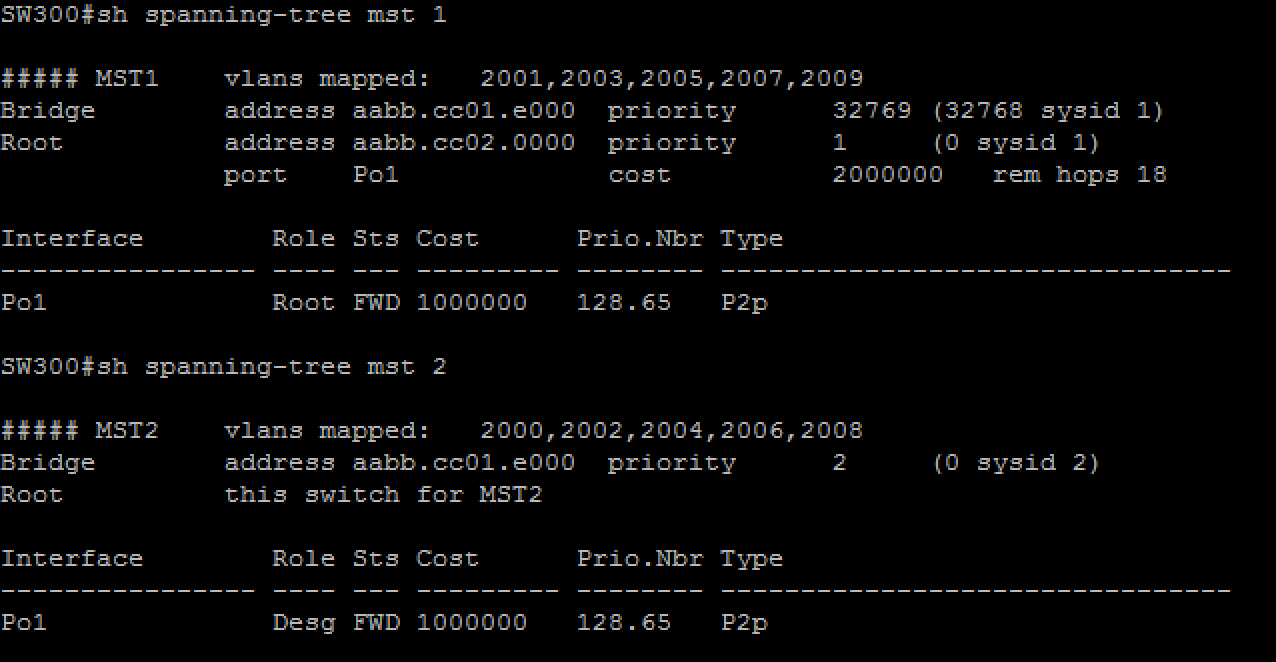
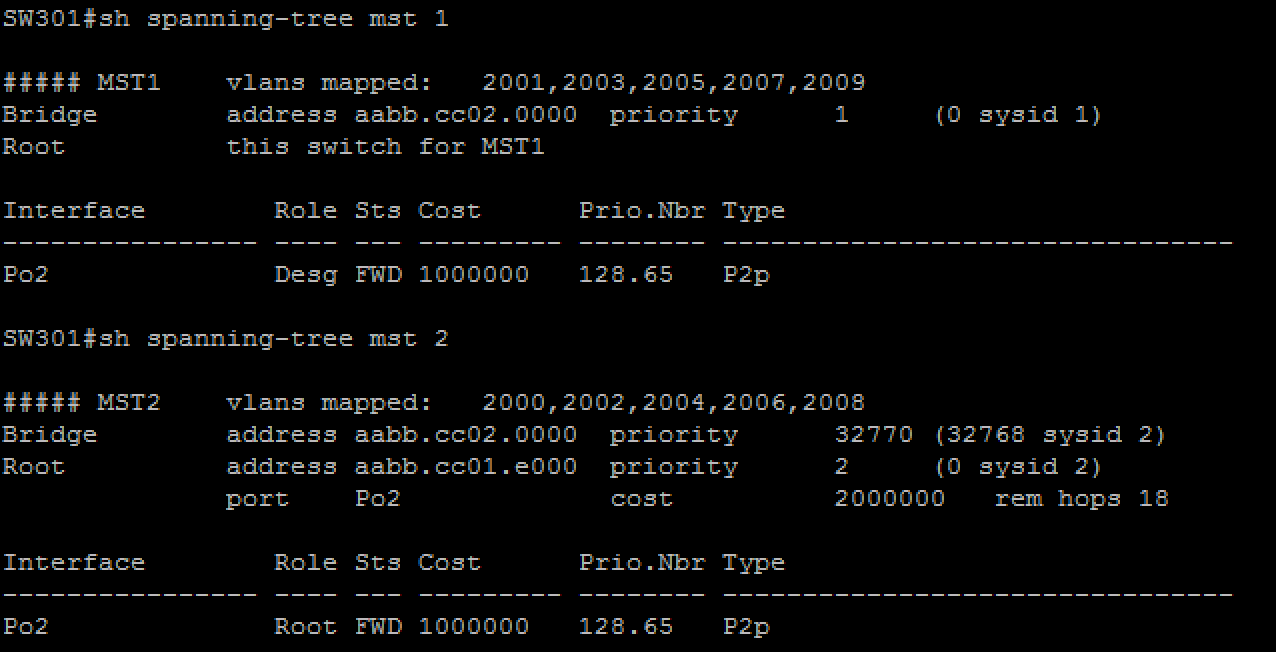
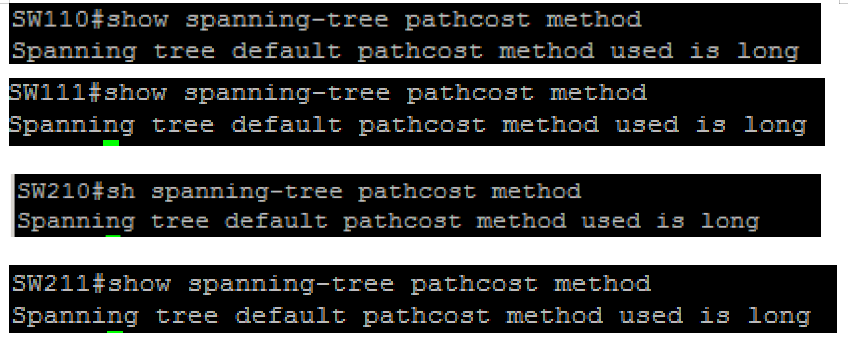
configure all access switches in both datacenter networks (SW110, SW111, SW210, SW211) as per the following requirements:
l use 32-bit based values for the default port path cost
l all four switches must use the default value for their interface cost
section 1.4: WAN switching technologies
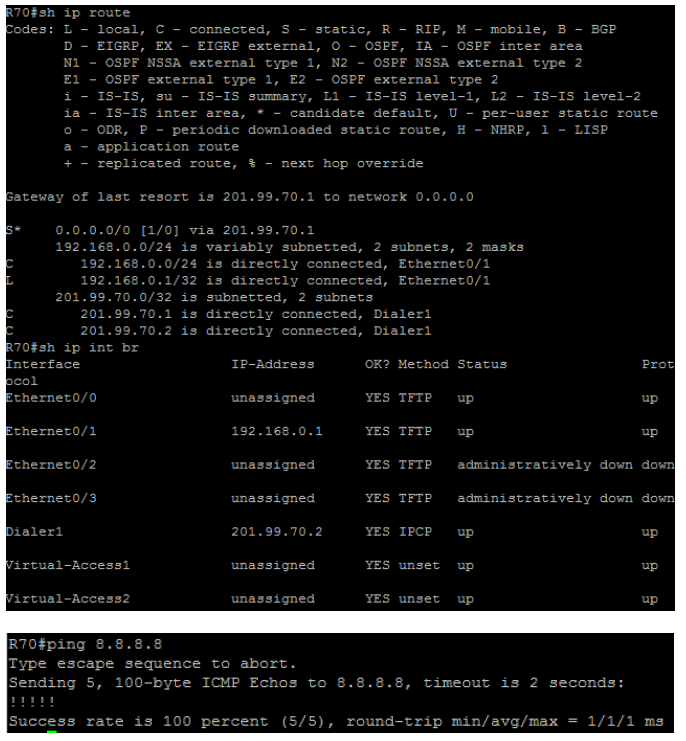
configure the home router R70 as per following requirements:
l the Ethernet WAN link must rely on a layer 2 protocol that supports authentication and layer 3 protocol negotiation
l the service provider expects that R70 completes a three-way handshake by providing the expected response of a challenge requested
l R70 must use the hostname “R70”and password “CCIE” (without quotes)
l R70 must receive an IP address from R8 and must install a default route pointing to 201.99.8.8
l ensure that R70 can successfully ping 8.8.8.8, which is located in the ISP#2 cloud
l you are not allowed to configure any static route in R70 in order to achieve the previous requirements
l use the pre-configured Dialer 1 interface as appropriate
section 2 layer 3 technologies
section 2.1: OSPF in HQ
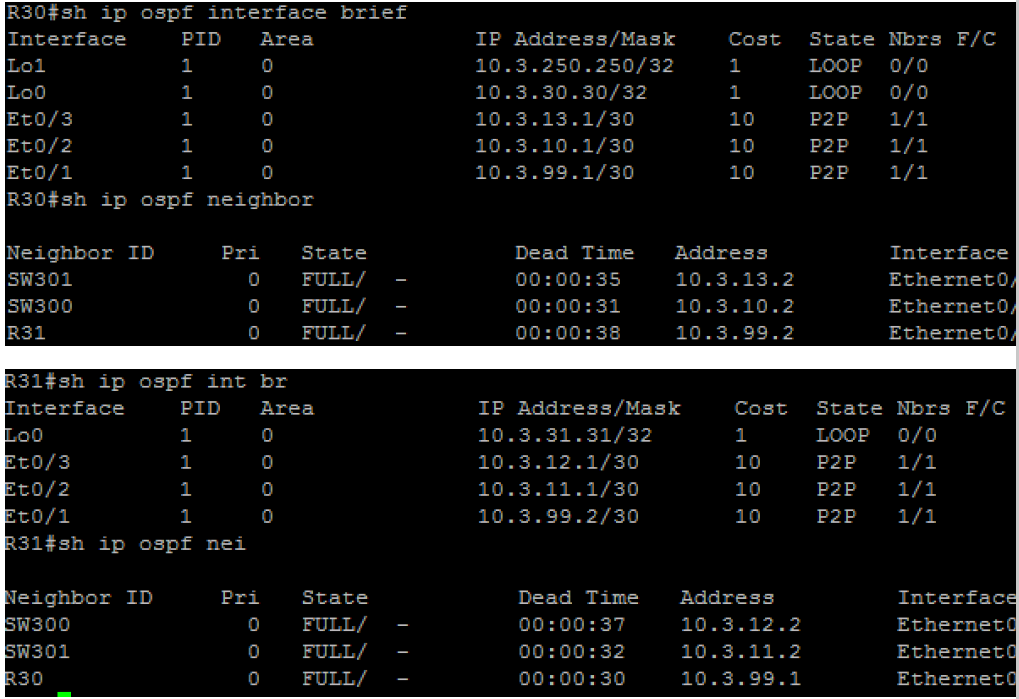
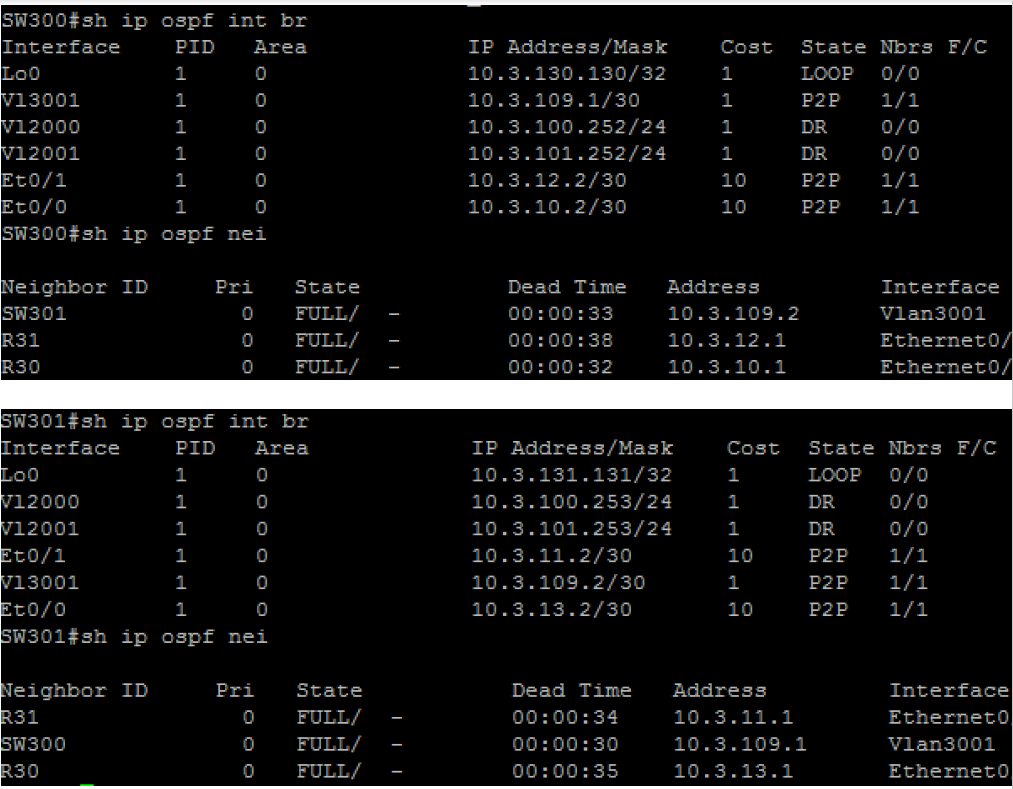
configure the headquarters network (BGP AS#65003) as per the following requirements:
l both gateway routers of the headquarters network must always advertise a default route into the ospf domain
l all four devices produce the exact same output as shown below. everything must match, except the “dead time” counters and line order
section 2.2: OSPF in DC#1
in order to speed up OSPF convergence in the datacenter#1 network, limit the number of IP prefixes that are carried in OSPF LSAs that OSPF is preconfigured in all required devices in datacenter#1
configure the datacenter#1 network as per the following requirements:
l all OSPF devices must exclude the IP prefixes of connected networks when advertising their type 1 router LSA, except for prefixes associated with loopbacks or passive interfaces
l host loopbacks are the only OSPF intra-area prefixes that may appear in any DC devices ‘routing table
l your solution must still apply if any new interface was added to the OSPF domain
l don not use any prefix-list or another explicit filter anywhere
l do not configure any interface as unnumbered
l do not remove any pre-configuration
section 2.3: B2B connection with partner#1
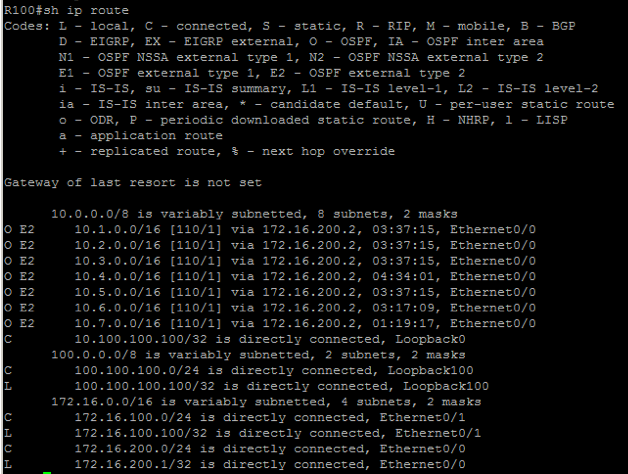
R100 is located in the partner#1 network and is connected to R42. it supports OSPF only. configure the large office network as per the following requirements:
l R42 must run a separate OSPF process with R100
l as mentioned in item 2.6, the site gateways R40 and R41 area not allowed to redistribute OSPF into BGP and vice versa
l R42 is allowed to redistribute OSPF into BGP and vice versa
At the end of the exam:
l The server 2 (that is located in the Datacenter#2) must be able to ping the IP address 100.100.100.100/24 (that is located in the partner#1 network)
R100, the partner router, must receive the external prefixes as shown below and no other prefixes:
Section 3 VPN Technology
Section 3.1: MPLS VPN
Section 3.2: DMVPN
Section 3.3: Internet Access
Section 3.4 LAN to LAN IPsec
Section 4 Infrastructure Security
Section 4.1: Device Security
Section 4.2: Network Security
Section 5 Infrastructure Security
Section 5.1: System Management
Section 5.2: Quality of Service
Section 5.3: Network Services
Section 5.4: Network Services






