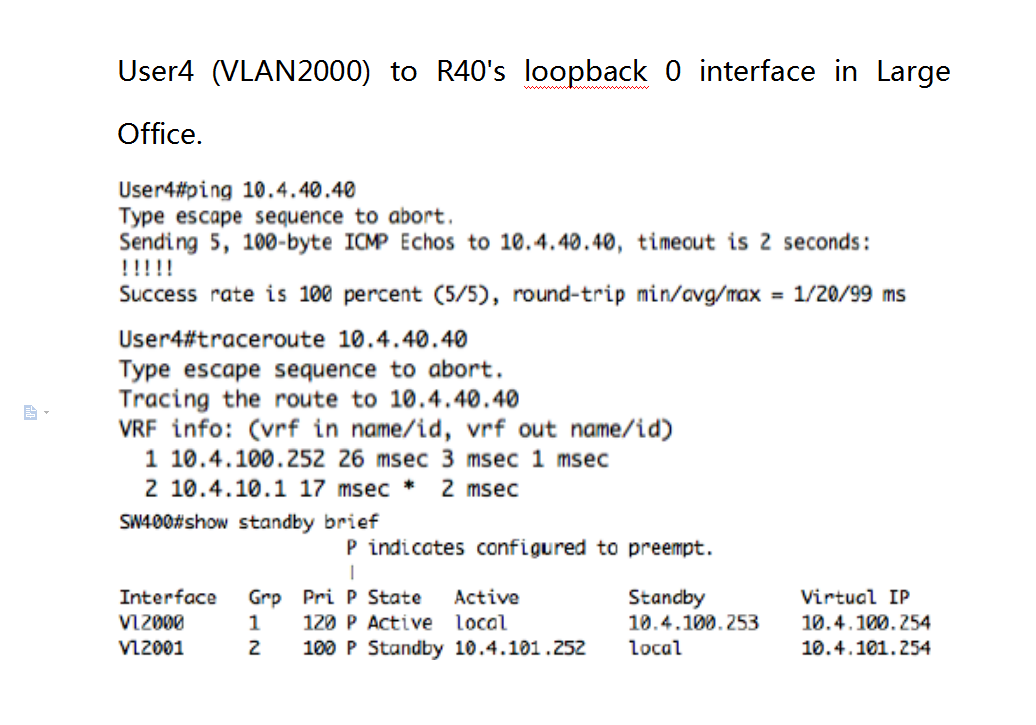
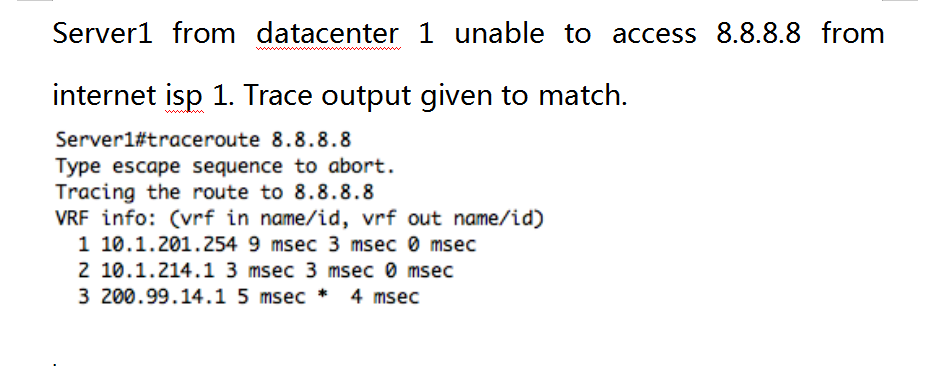
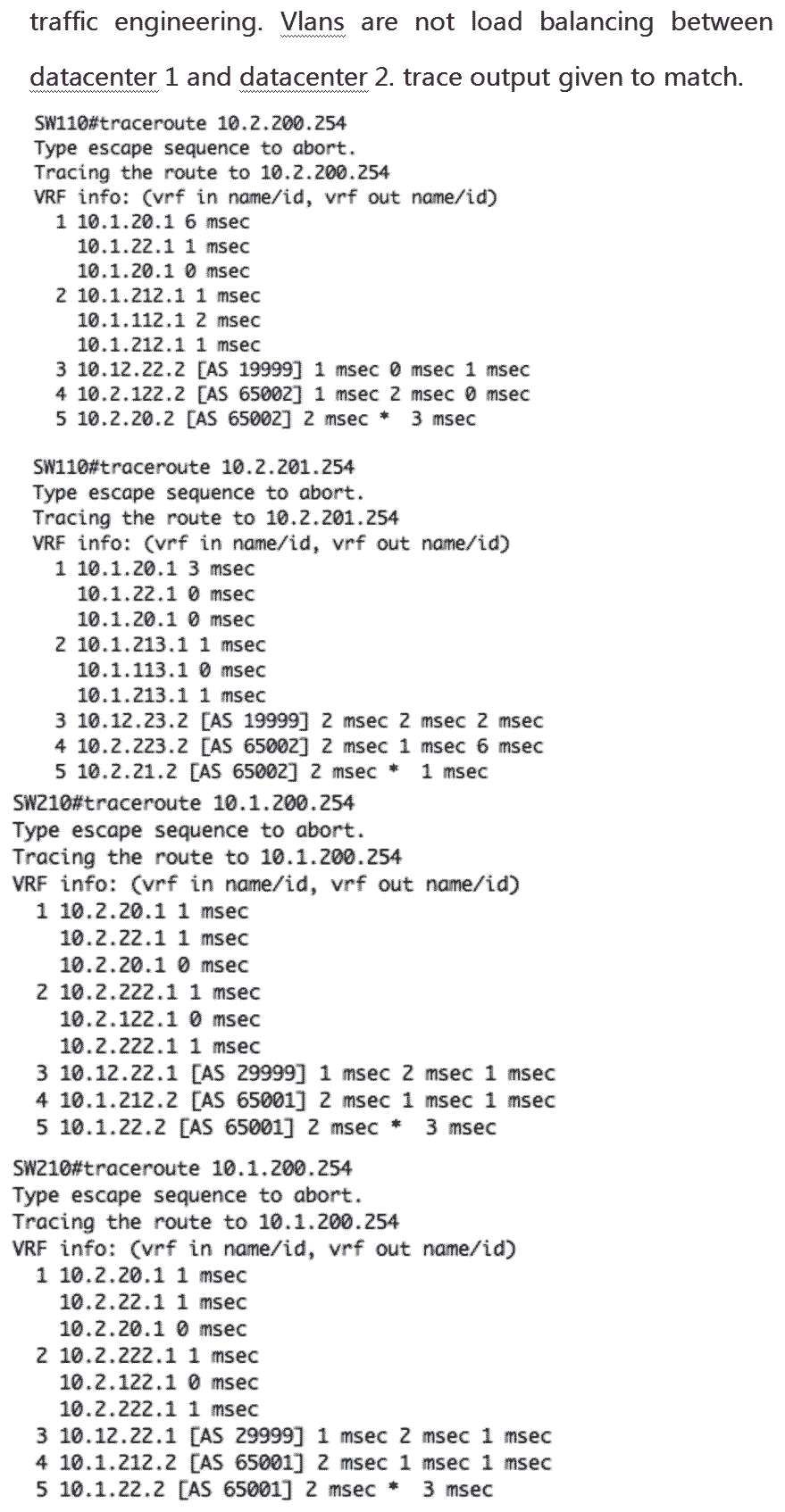
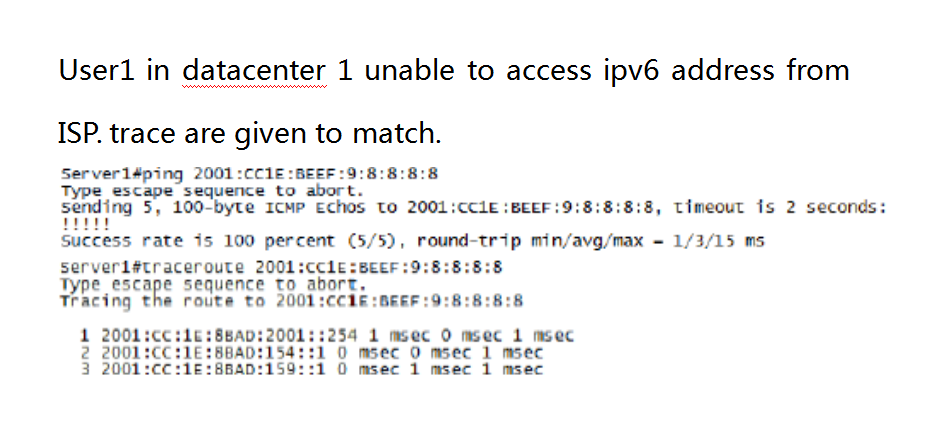
ccie v5 lab
-
- 1687 Reviews
student has been coming for several months, the experiment is also
The whole written test preparation process is to turn over all kinds of
2.standard hdlc: an environment that supports only a single protocol
Show ipv6 route
Interface Serial0
1. Switch and bridge
R14(config-if)#dialer-group 9
=========================================================== ===============
The leftmost 0 of a segment can be removed.
and opening my own computer company. There
more difficulties when they come to work, the teacher should use the
172.16.3.1
=========================================================== ===============
This is not the end point, not even the starting point of the end point, but it may be the end point of the starting point. --Winston Churchill
Redundant topology , causing " broadcast storm ", " multiple frame reception ", "MAC address table instability ".
Spanning-tree vlan 1 priority ?
See " Who " is logged in locally
A: 10.0.0.0/8
View the CDP information of an interface .
IGRP uses composite metrics to select the best route .
Q8: D version CP snooping, add a trust, and then remove the D version of the CP lease
=========================================================== =====================
VTP has three modes :
=========================================================== ===============
Ip add 10.1.1.1 255.255.255.0
experimenting with bottles and cans for four years. After graduation, I
worst is cit, I can't believe it can, I have all the analysis of the
6. Opportunities and platforms
Time Node 7: I entered the VIP customer delivery team Team with a 6-month trial period different from ordinary people.
Have a link state database ( network map )
Point out specific neighbors
Na.
complicated situation in my work. At that time, the superstition of mcse
1. Define the maximum number 2. Horizontal separation 3. Route poisoning , toxicity reversal
RA———update———RB
the beginning, they thought of themselves very high. They thought that
want to tell you that if you don't plan for future work in the current
2001::2 2001::1 192.168.1.1 192.168.1.2
X.x.x.x has always been useless, and finally checked the English CD for a long time, finally knowing the Cisco NO series command, this is my first debugging experience. I was thrilled by the moment of Internet access! A series of doubts about myself since the university have been swept away.
IGRP use have to be 24bit measure .
Network 192.168.1.0 0.0.0.3
Private adoption has IP host address , can not directly access the public network (Internet)
Lab 5-2: Configuring Active/Active High Availability
Configuring and Verifying Transparent Firewall Layer 3 Through Layer 7 Access Controls
!
This
Configuring and Verifying Object Groups
Point out specific neighbors
Look at the picture and see the configuration.
it was ccie, and they could enjoy higher rewards. When they really
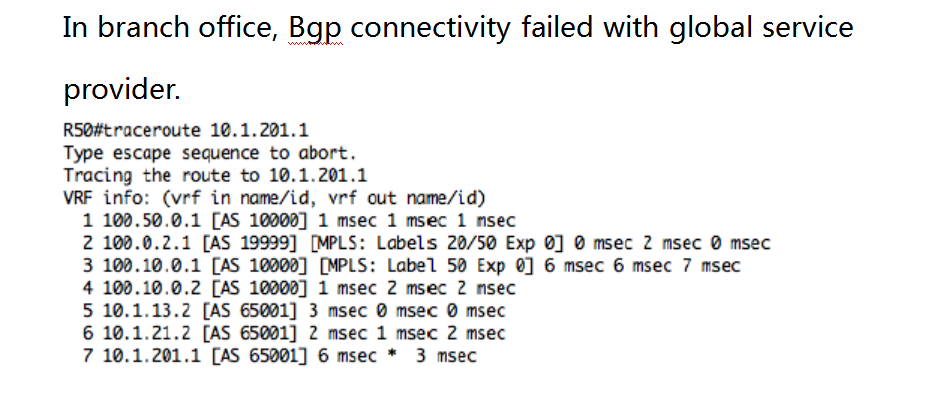
The second place of TR: Change the IP address of R52 (not the pre-configured IP address error, because it is confirmed that UP is configured when EBGP is configured)
Encryption system all plaintext passwords ( weaker )
talk about mpls in the afternoon. Although I am already familiar with
B(config)#inte s 1
Debug neighbor creation process
As number is the autonomous system number ( autonomous domain )
Enable secret
day and see them all in the lab to solve a problem. They have a passion for technology and they are not just for a paper certificate. But
is always no way to make a lot of money. Sometimes the income of a
can bear How much responsibility, your ability is reflected in how much you have resolved and how to solve problems. Without
B(config-if)#ip nat inside
FFXY X=1 temporary X=0 fixed; Y indicates range Y=2 link Y=5 site Y=E global
2.AUX port ( auxiliary Management Interface ): can be linked access MODEM remote management , exclusive manner .
vtp password with opposing VTP password
Frame-relay route 120 interface Serial0 110
1. Static State N A T 2 . Dynamic state N A T . 3 . P the AT
16. Can I compare MEDs between multiple ASs? If yes, do you need the prerequisites? If so, what are the prerequisites?
and attacks at night, do experiments late at night, listen to myself
1. RIPng is developed based on RIPv2, classless routing
Ten years of life and death, knocking on the version, to dawn. Thousands of orders, troulbe is hiding everywhere. How much more about the feature, nausea and stagnation. V1V2 turns, every day, every night, CCIE, pass busy
3. Telnet: multi-person remote management ( depending on performance , number of VTY lines ). Not safe .
B(config)#inte s 1
If PCA wants PCB communication, the destination address is IPV6 address because it is IPV6 terminal itself.
Those hosts can be predetermined feed line N A T
Encapsulation frame-relay
0 : represents no cache
Troubleshooting Active/Active Failover
Private There IP public network router will not appear in the routing table .
9. What is the reason for selecting a backbone or metropolitan area network for ISIS and OSPF?
18. There are still ten minutes to cut back and limit the retreat. The cutover has not been successful. The bureau has already urged you to retreat. But you think that if you try these problems for another 5 minutes, you may solve it. What is your choice?
To apply for Cisco's gold and silver agents, you must need a certain number of CCIEs, including 4 for gold medals, 2 for silver medals, and a lot of big projects to bid. When bidding, the company with CCIE can specify the price. How many points are added. These are the real benefits of CCIE!
Configuring and Verifying Other Basic Access Controls
The 3550 supports 802.1Q and
Q10: The R24's outside configuration is added, and the R25 can be added in parallel. (The address of telnet is 123.45.67.89)
1.IPV6 address type and format
face the difficulties. Many
NAT on Cisco ASA Software Version 8.2 and Earlier
ACL two actions :
voice and ** traffic, and are accessed by a variety of wireless devices.
10.1.1.1/0.0.0.0
7. When to disconnect
FFXY X=1 temporary X=0 fixed; Y indicates range Y=2 link Y=5 site Y=E global
2) Implicit security: When an FTP client connects to an FTP server, implicit security will automatically start running with the SSL connection. In implicit security, the server defines a specific port (TCP port 990) for the client to establish a secure connection with.
Those hosts can be predetermined feed line N A T
should train more independent people, especially people. We must
hour old, and always had more than 90 points. He began to know that
A server:
Target port :
Configuring and Verifying Basic Device Management Settings
6:50 AM Departure
2. Storage forwarding : slow speed , to ensure the correctness of the frame being forwarded .
On the interface enabled with PPP
A section of configuration:
2950 supports only support 802.1Q thoroughfares agreement
Vlan 10 name cisco
Encapsulation PPP
Ipv6 address 3FFE: FFFF: 1:: 1/64
=========================================================== ================
OSPF supports only support IP network environment , supports only the equivalent load balancing
Lesson 3: Configuring Cisco ASA Adaptive Security Appliance Routing Features
Copy tftp: running-config
Destnation Network IP: target network network IP
Show controllers serial 0
What
PS: The actual situation is about 10 minutes earlier than the scheduled one. . . . . The night before, I basically woken up every hour during my sleep at night, but it was good to sleep at 8 o'clock, and it was OK to add up.
Basic Stateful Inspection Tuning Features
are two sets of instructions, in addition to rote memorization or rote
stay at the lowest level of technology for a long time.
2.0.0.0
FF02::1:FF (104 bits) The last 24 bits are pending, and the neighbor requests a multicast address.
Use multicast to route notifications ( reliable )
Set set login password when
I am very pleased to feel that I can afford this 1000 yuan per door. The
Show cdp entry *
Do you want to over write ? {confirm} (Enter)
Configuring and Verifying Transparent Firewall Layer 2 Access Controls
=========================================================== ===============
ACL two actions :
6. Set when to dial the number
=========================================================== ===============
The content, currently in development, may include real-world applications that involve:
3. Telnet: multi-person remote management ( depending on performance , number of VTY lines ). Not safe .
Serial1 is administratively down, Line protocol is down
12. Why do the backbone network pop and metro network exits be next-hop-self?
Q: Since you got multiple CCIE qualifications, what projects have you done and what role did you play in it?
=========================================================== ==============
(3) CCIE is more expensive
To understanding
Tone test PPP identity verification .
Interface Serial0
Show version
Module 3: Network Integration
Your value
A segment is all 0, can only be represented by a 0
Q2: R14, next-version op-self
Check to see CDP neighbor ( containing three layers of the IP address )
Q8: D version CP snooping, add a trust, and then remove the D version of the CP lease
As the software takes longer and longer, I find it harder and harder to make software. Where is it difficult? How to make a good software. What are the good software standards? Two words, easy to use, good-looking! The greatest value of programmers is the ability to make good and good-looking software.
work. From
Many commands on Cisco devices can be used by replacing IP with IPV6.
Agreement :
3. IPV6 packet structure is simpler and the forwarding efficiency is higher.
1. Media type : twisted pair , coaxial cable , fiber
Ccie
22. In general, how many spanning trees does the L2 switch have?
2. with set ACL reject absolutely london to Ping through Denver (1)
2. Which routes are included in the routing table of isis level1? When there are multiple level-1-2 exits, where do other routes learn from, how to choose a route?
Enter the vlan Mode
I haven't come and updated for a long time. The past personality is basically a classic case study every month. Why is this blog that has been closed for nearly six months? Let me review the efforts of this time.
2. Use the USB to console cable to connect the router to the PC first, and use the CRT login software to configure it.
Point out specific neighbors
I am very pleased to feel that I can afford this 1000 yuan per door. The
What are the characteristics and advantages of IPV6 compared to IPV4?
Basic configuration: modify the host name, privileged password, configure the console port password, configure telnet, ssh; divide Vlan
Interface Serial1
Interface serial 0
Source :
Change the boot characteristics? y/n [n]: n (select no)
Vlan 10 name cisco
asked if I have touched 36xx, 72xx, and the job opportunity is At hand, I can only say that I have touched my head and can handle it. I think I can get an np in two weeks. Can I make a 36 for two nights? The
=========================================================== ===============
Master Wu Xue is waiting for him to say something. Obviously he is not satisfied with the apprentice's answer. Finally he spoke up: "You haven't gotten to take the black belt. Come back a year later."
Let's first use the A server to ping the B server. Can it pass? We are going to analyze the process positively:
Cisco ASA Adaptive Security Appliance Licensing Options
Only one primary IP can be configured for one port, but multiple secondary IPs can be configured.
FRAME-REL A Y will also cause routing unreachability problems, ie horizontal separation rules.
1.CONSOLE PORT ( management console interface ): distance limit , exclusive way .
RIPng test
Concept :
Interface xxx
Copy tftp: running-config
R14(config)#isdn switch-type basic-net3
Basic Stateful Inspection Tuning Features
think every one in front of me is a path to change your destiny. As long
the course. I am ready to go back to rest at two o'clock. I
Rommon9>set(View)
=========================================================== ================
!
Static default route: ipv6 route ::/0 serial 1/0
The running-config copy to tftp the service
The metric is 32 bits long , the K values are not equal , and the neighbor relationship cannot be created . The AS autonomous system is different ,ccie v5 lab, and the neighbor relationship cannot be created.
real ccie value, borrow a netizen's words: "Huangsha hundred wars wear
Debug ip igrp transactions
1. Static State N A T 2 . Dynamic state N A T . 3 . P the AT
Q4: The demand has changed, not SERVER1, but SERVER2, the solution is consistent.
In the past six months, almost every day, one hour before the company (8:00, the company went to work at 9:00), why? Learning, in order not to affect my job, I have pushed away all kinds of social activities and even a lot of time with my wife to go out to watch movies, go shopping, exercise, wash dishes, buy food and cook, etc., no longer worry do. on Saturday
B(config)#ip nat inside source static 192.168.1.10 1.1.1.1
to the actual needs in the work, I returned to Kunming after the first
Typical application environment PCA - R (dual stack router) - PCB
was a good friend to eat, and I was too embarrassed to pay the bill. One voice is unsatisfactory. Second, if you want to pay back, you may have to be hungry this month.
Main class network number ABC number
N A T three types :
Cisco MPF Overview
late at night. The
and opening my own computer company. There
Another point is that in order to maintain the value of CCIE and prevent oversupply, Cisco has a certain amount of control over the growth of CCIE every year. Now it is about 1,000 people per year worldwide! Fully synchronized with Cisco's product sales growth pace!
If you transfer binary files in ASCII mode, they will still be translated even if they are not needed. This will corrupt the data. (The ASCII mode generally assumes that the first significant digit of each character is meaningless because the ASCII character combination does not use it. If you transfer binary files, all bits are important.)
In August of this year, I personally worked in a place where I worked for three years, but in the past three years, I have reviewed the efforts I have made during this period. There are many sighs and many regrets, but fortunately I am used to writing similar The habit of “following” has recorded a lot of work from the work in 2014 to the present. Including success also includes failure. I have been looking for a half-day holiday to relish the following content. I have been thinking that when I was nearly 40 years old, I wanted him to become a personal book and stay with me.